Your Chinese-made CAC Reader from Amazon is a national security threat.
The Hidden Risk of Chinese-Made CAC Readers
Every servicemember with a Common Access Card (CAC) has, at some point, had to check email or log into a DoD website from a personal computer.
That’s not prohibited—and it probably shouldn’t be. Accessibility has to be balanced with security.
But here’s what most people don’t realize: the CAC reader itself is the first line of defense when accessing U.S. military systems. And where you buy that little piece of hardware matters a lot.
If it’s made in China, that should set off alarm bells.
The Threat Hiding in Plain Sight
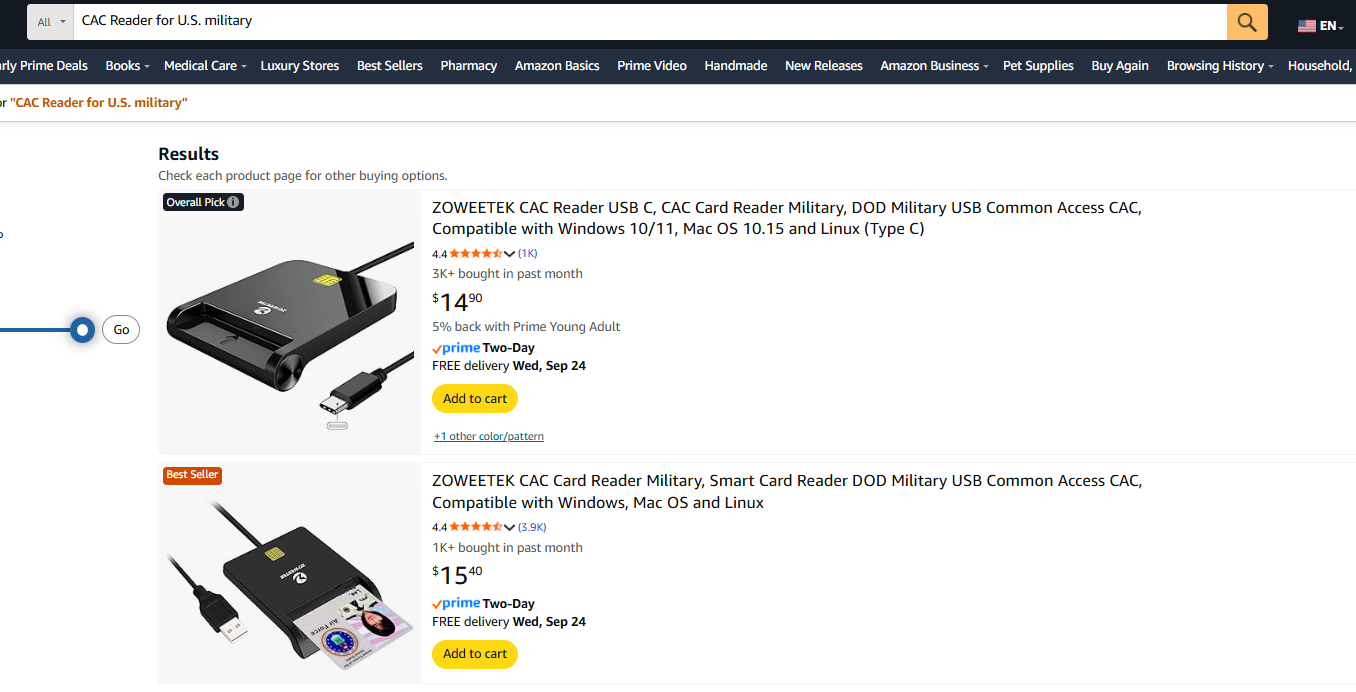
Search Amazon for “CAC Reader for U.S. Military” and the top result is a Chinese-made device from Zoweetek, a company based in Shenzhen.
Over 3,000 people bought this reader in the past month alone. That means thousands of servicemembers, DoD civilians, and contractors are plugging a Chinese-manufactured device directly into their computers.
And the listing doesn’t even try to hide its audience. The full title:
“ZOWEETEK CAC Reader USB C, CAC Card Reader Military, DOD Military USB Common Access CAC, Compatible with Windows 10/11, Mac OS 10.15 and Linux (Type C).”
This isn’t subtle—it’s a direct pitch to the U.S. military community. And Zoweetek is just one of hundreds of similar Chinese vendors pushing these devices online right now.
Everyday Hardware, Strategic Risk
Most consumer electronics in the U.S. are made in China. For phones, headsets, or cheap chargers, that’s one thing.
But when it comes to critical authentication devices for military systems, it’s a whole different story.
You wouldn’t plug a random USB stick into your laptop. The same principle should apply here.
At the government level, CAC readers must be listed on the DoDIN Approved Products List (APL) to ensure they’re secure. But at the personal level? Chinese readers are being used daily by thousands of DoD personnel.
That’s a massive and preventable risk.
Cybersecurity Is National Security
Supply chain security isn’t just technical—it’s strategic.
China is a peer adversary with both the capability and intent to challenge U.S. power. Relying on Chinese-made hardware in our most sensitive systems hands them unnecessary leverage.
Right now, no one can say for certain what these devices are doing behind the scenes. Reverse engineering is needed. If you’re a security researcher who wants to take a closer look, consider this your invitation.
What You Should Do
If you already own a Chinese-made CAC reader: don’t keep it, and don’t give it away to another servicemember.
Here are safer options:
- Buy from your local military exchange.
- Use one issued by your employer, if available.
- If you must order online, choose a TAA-compliant device (U.S. or allied manufacturing only).
What Amazon Should Do
Amazon has a responsibility here. The company works closely with the U.S. military through AWS contracts worth billions. It cannot also be the storefront selling Chinese-made “military CAC readers.”
Amazon should:
- Delist CAC readers from Chinese vendors.
- Ban misleading product titles that explicitly target DoD personnel.
Right now, the first search result for “CAC Reader Military” is a Chinese product. That’s unacceptable.
Final Thoughts
Servicemembers will keep using these devices unless they know better. And most don’t.
This is a systemic problem that requires Amazon and other platforms to step up. Until then, the risk remains on the shoulders of individuals.
Cybersecurity is national security—and even something as small as a CAC reader can become a vector for compromise.
Stay vigilant.





